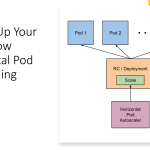
Kubernetes has become one of the most popular container orchestration tools, and Azure Kubernetes Service (AKS) is a managed Kubernetes service provided by Microsoft Azure. With the increasing use of Kubernetes and AKS, there is a growing need to improve the security and management of access to cloud resources.
AKS pod managed identity is a feature of AKS that simplifies the management of access to Azure resources by creating an identity for each pod in a Kubernetes cluster. The AKS pod managed identity allows the pods to access Azure services securely without the need to manage credentials, passwords, or access tokens.
In this blog post, we’ll take a closer look at what AKS pod managed identity is, how it works, and its benefits.
What is AKS Pod Managed Identity?
AKS pod managed identity is a feature of AKS that enables the management of identities for pods in a Kubernetes cluster. When a pod is created with AKS pod managed identity enabled, a Managed Identity is automatically created for that pod. This Managed Identity is then used to authenticate the pod with Azure services such as Azure Key Vault, Azure Storage, and Azure SQL Database, among others.
AKS pod managed identity eliminates the need for storing secrets and credentials within the pod’s configuration, which can improve the security of the pod and simplify the management of access to cloud resources.
How AKS Pod Managed Identity Works
AKS pod managed identity uses Azure’s Managed Identity service, which is a feature of Azure Active Directory (AAD). When a pod is created in an AKS cluster with pod managed identity enabled, a Managed Identity is automatically created for that pod.
To use AKS pod managed identity, you must first enable the feature in your AKS cluster. This can be done using the Azure CLI or through the Azure portal. Once enabled, you can then create a Kubernetes manifest file that includes a ManagedIdentity resource definition for each pod that needs to access Azure resources.
Here’s an example of a Kubernetes manifest file that uses AKS pod managed identity:
#yamlapiVersion: v1 kind: Pod metadata: name: my-pod spec: containers: - name: my-container image: my-image env: - name: AZURE_TENANT_ID value: "<tenant-id>" - name: AZURE_CLIENT_ID value: "<client-id>" - name: AZURE_CLIENT_SECRET valueFrom: secretKeyRef: name: my-secret key: my-secret-key identity: type: ManagedIdentity
In this example, the identity section defines a Managed Identity for the pod using the type: ManagedIdentity field. The AZURE_TENANT_ID, AZURE_CLIENT_ID, and AZURE_CLIENT_SECRET environment variables are also defined, which allow the pod to authenticate with Azure services using its Managed Identity.
Once the pod is created, you can then grant it access to Azure resources by assigning it the appropriate role or permissions. This can be done using Azure’s Role-Based Access Control (RBAC) system or through other access control mechanisms provided by Azure services.
Here’s another example manifest file that demonstrates how to use AKS Pod Managed Identity:
#yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: my-app
spec:
replicas: 1
selector:
matchLabels:
app: my-app
template:
metadata:
labels:
app: my-app
spec:
containers:
- name: my-app
image: myregistry/my-app:v1
ports:
- containerPort: 80
env:
- name: AzureServicesAuthConnectionString
value: RunAs=App;AppId=<app-id>;TenantId=<tenant-id>;AppKey=<app-key>
identity:
type: ManagedIdentity
In this example, the identity section defines a Managed Identity for the pod using the type: ManagedIdentity field. The AzureServicesAuthConnectionString environment variable is also defined, which allows the pod to authenticate with Azure services using its Managed Identity.
Once the pod is created, you can then grant it access to Azure resources by assigning it the appropriate role or permissions. This can be done using Azure’s Role-Based Access Control (RBAC) system or through other access control mechanisms provided by Azure services.
Benefits of AKS Pod Managed Identity
AKS pod managed identity provides several benefits, including:
Improved security
AKS pod managed identity eliminates the need to store credentials or access tokens within the pod’s configuration. This reduces the risk of accidental exposure of sensitive data and improves the overall security of the pod and the cluster.
Simplified management
AKS pod managed identity simplifies the management of access to cloud resources by creating an identity for each pod in a Kubernetes cluster. This eliminates the need to manage service principals or credentials manually, which can reduce the administrative overhead and improve the efficiency of the cluster.
Greater flexibility
AKS pod managed identity provides greater flexibility by allowing you to grant access to Azure resources at a more granular level. You can assign roles or permissions directly to individual pods, which can reduce the risk of unauthorized access and improve the overall security posture of the cluster.
Easier compliance
AKS pod managed identity can make it easier to comply with regulatory requirements such as GDPR, HIPAA, and PCI DSS. By eliminating the need to store secrets and credentials within the pod’s configuration, you can reduce the risk of non-compliance and simplify the auditing process.
Better scalability
AKS pod managed identity can help improve the scalability of your Kubernetes clusters by reducing the overhead associated with managing service principals or credentials manually. This can enable you to scale your clusters more easily and efficiently, which can improve the overall performance and availability of your applications.
Conclusion
AKS pod managed identity is a powerful feature of AKS that can simplify the management of access to Azure resources, improve the security of your pods and clusters, and help you comply with regulatory requirements. By creating a Managed Identity for each pod in your Kubernetes cluster, AKS pod managed identity can eliminate the need to manage credentials and access tokens manually, which can reduce the administrative overhead and improve the efficiency of your operations.
In addition to AKS pod managed identity, Azure provides other identity and access management features such as AKS managed identity and workload management identity that can help you manage access to your Azure resources securely. By using these features in conjunction with AKS pod managed identity, you can create a comprehensive identity and access management solution for your Kubernetes workloads in Azure.
References
- Use Azure Active Directory pod-managed identities in Azure Kubernetes Service (Preview)