AKS workload identity and AKS pod managed identity both provide a way to manage access to Azure resources from within a Kubernetes cluster. However, there are some key differences between the two features.
Scope
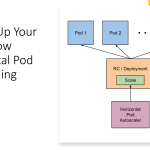
AKS pod managed identity provides a managed identity for each individual pod within a Kubernetes cluster. This allows you to grant access to Azure resources at a very granular level. AKS workload identity, on the other hand, provides a single AAD service principal for a Kubernetes namespace. This provides a broader scope for access to Azure resources within the namespace.
Access management
With AKS pod managed identity, you can assign roles or permissions directly to individual pods. This provides greater flexibility for managing access to Azure resources within the cluster. With AKS workload identity, access management is done through AAD roles and role assignments. This provides a more centralized approach to managing access to Azure resources within the namespace.
Security
AKS pod managed identity eliminates the need to store secrets or access tokens within pod configurations, which can improve the security of the Kubernetes cluster. AKS workload identity also eliminates the need to store secrets or access tokens within pod configurations. However, because the AAD service principal is shared by all pods within the namespace, there is a risk that if the service principal is compromised, all pods within the namespace could be affected.
In summary, AKS workload identity is a powerful feature of AKS that enables you to use Azure Active Directory to manage access to Azure resources from within a Kubernetes cluster. By creating a single AAD service principal for a Kubernetes namespace, AKS workload identity provides a centralized approach to access management. This can simplify the management of access to Azure resources and improve the security of your Kubernetes cluster.
While AKS pod managed identity and AKS workload identity both provide a way to manage access to Azure resources from within a Kubernetes cluster, they have different scopes and approaches to access management. By understanding the differences between the two features, you can choose the approach that best meets the needs of your organization.